AWS security groups act as a virtual firewall for your EC2 instances to control inbound and outbound traffic.
"Security groups act at the instance level, not the subnet level. Therefore, each instance in a subnet in your VPC could be assigned to a different set of security groups." - AWS Documentation
Trawling through your VPC flow logs helps provide visibility into your network traffic to detect anomalous traffic and provides insights, however, it still comes with its own risk of error.
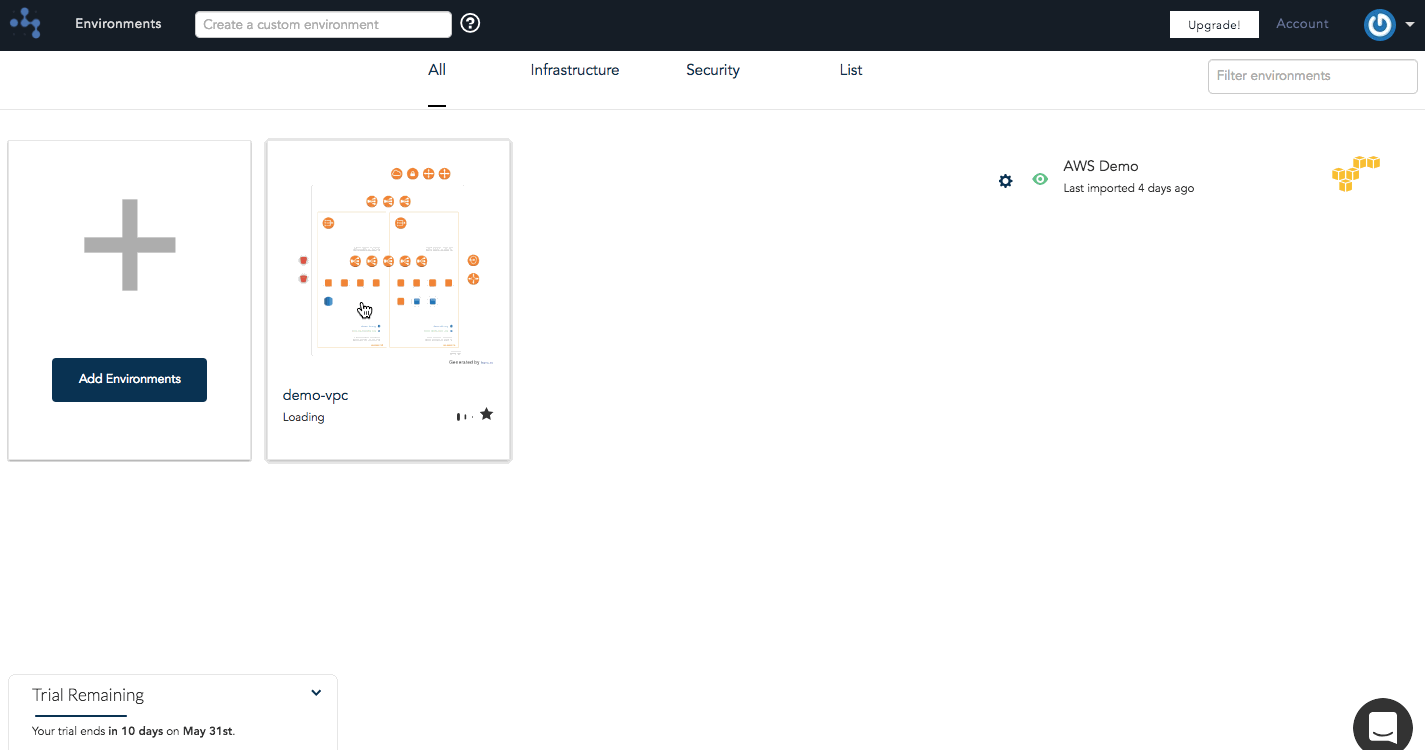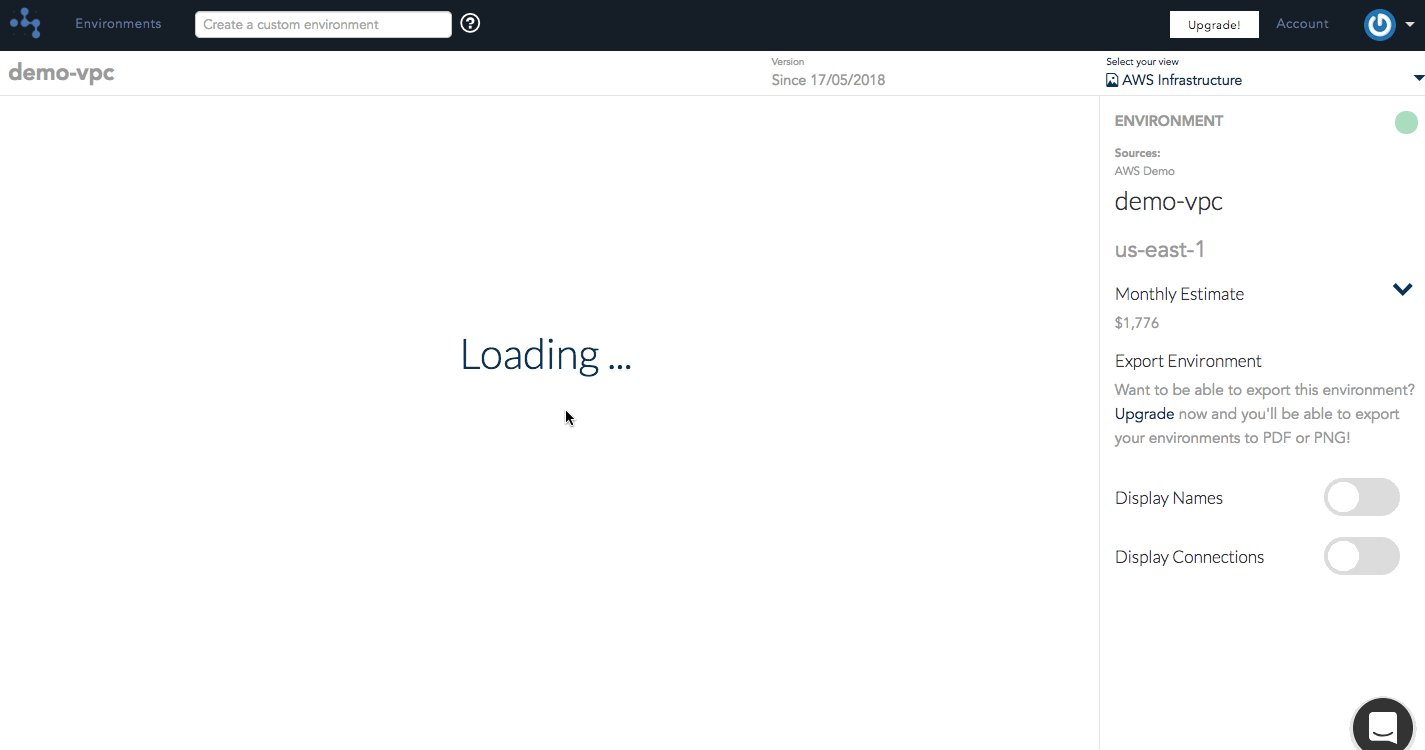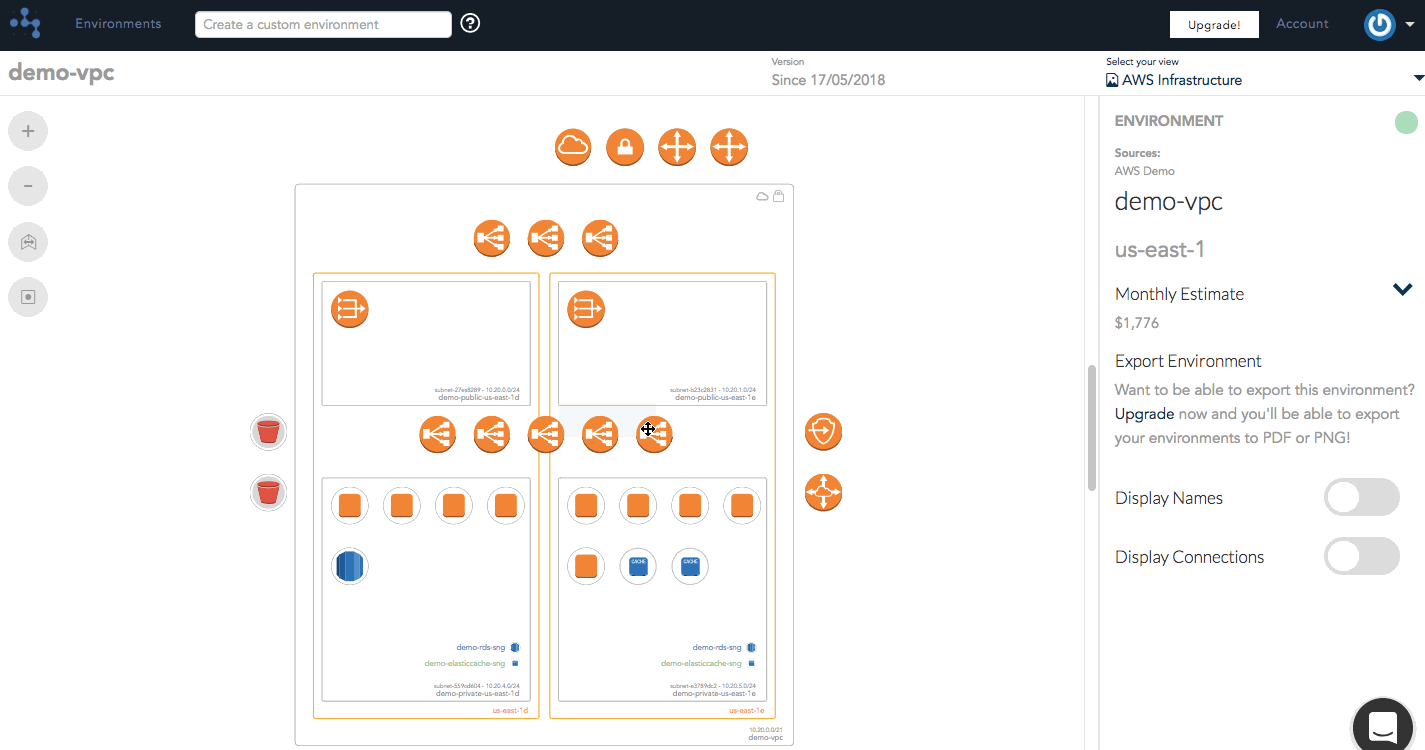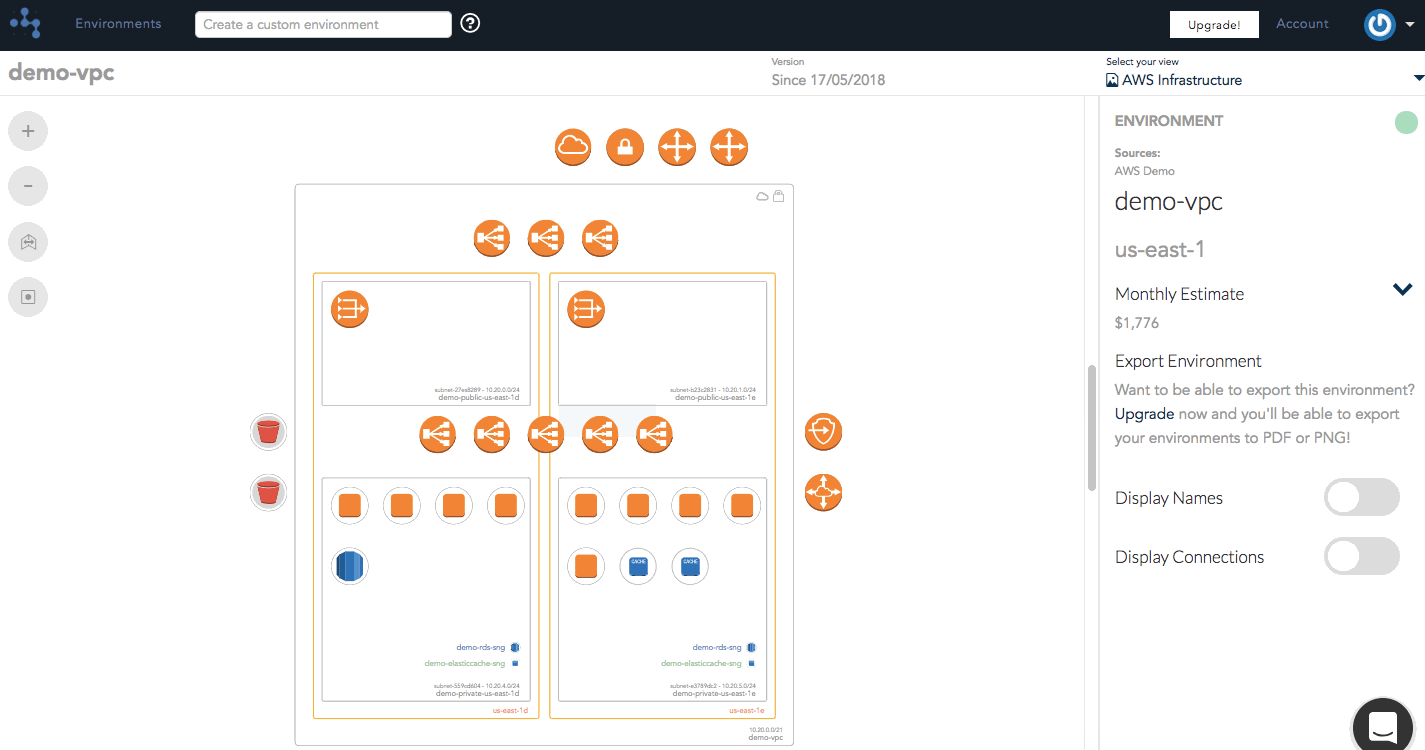
Generating a visual diagram from the source of truth with automated layouts to display your network infrastructure as it is right now can eliminate the potential risk of human error.
Hava offers several ways to assist with diagnosing security within your network.
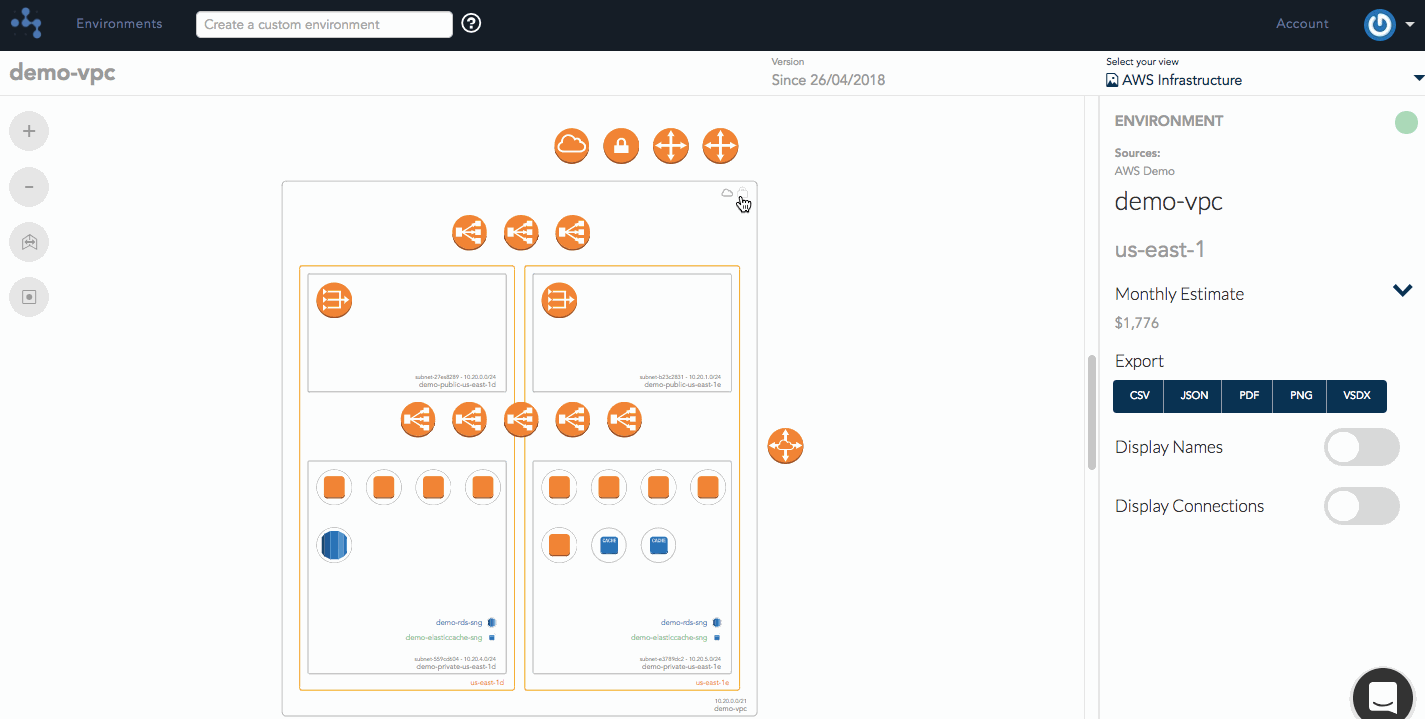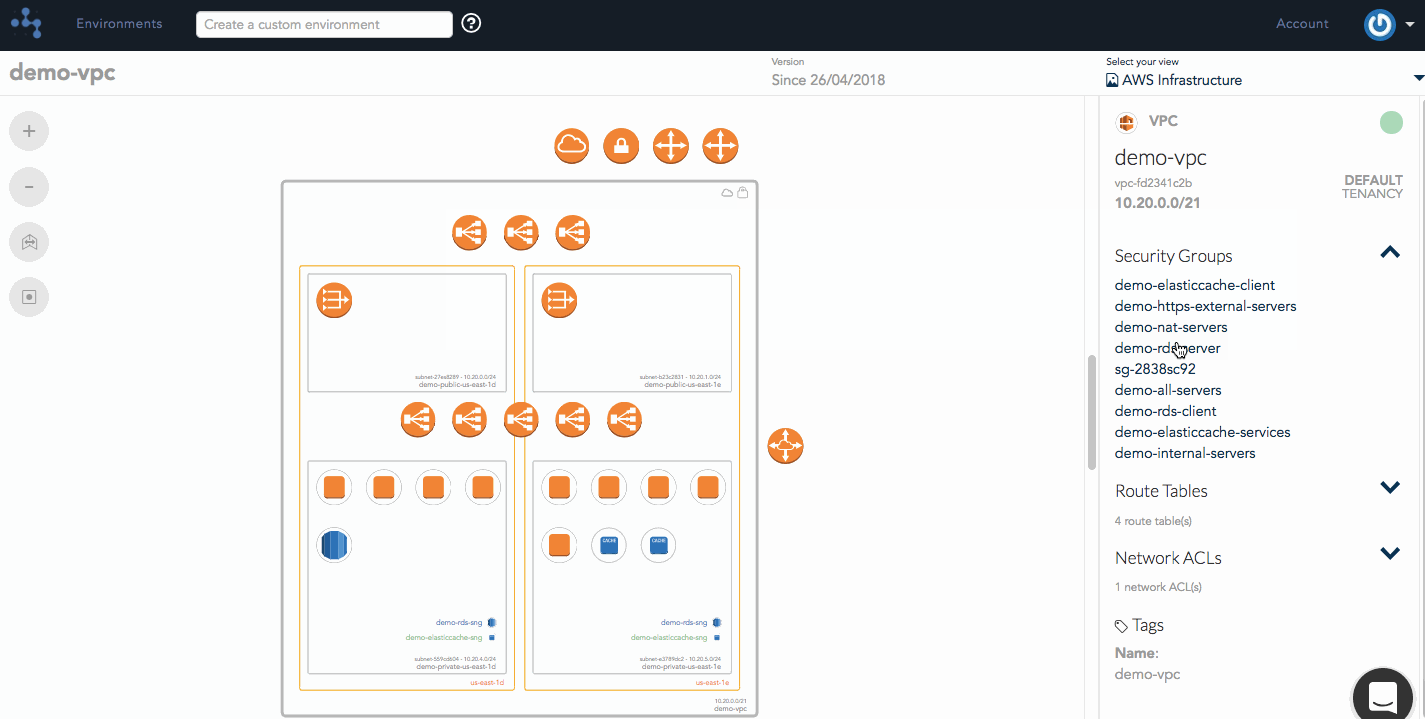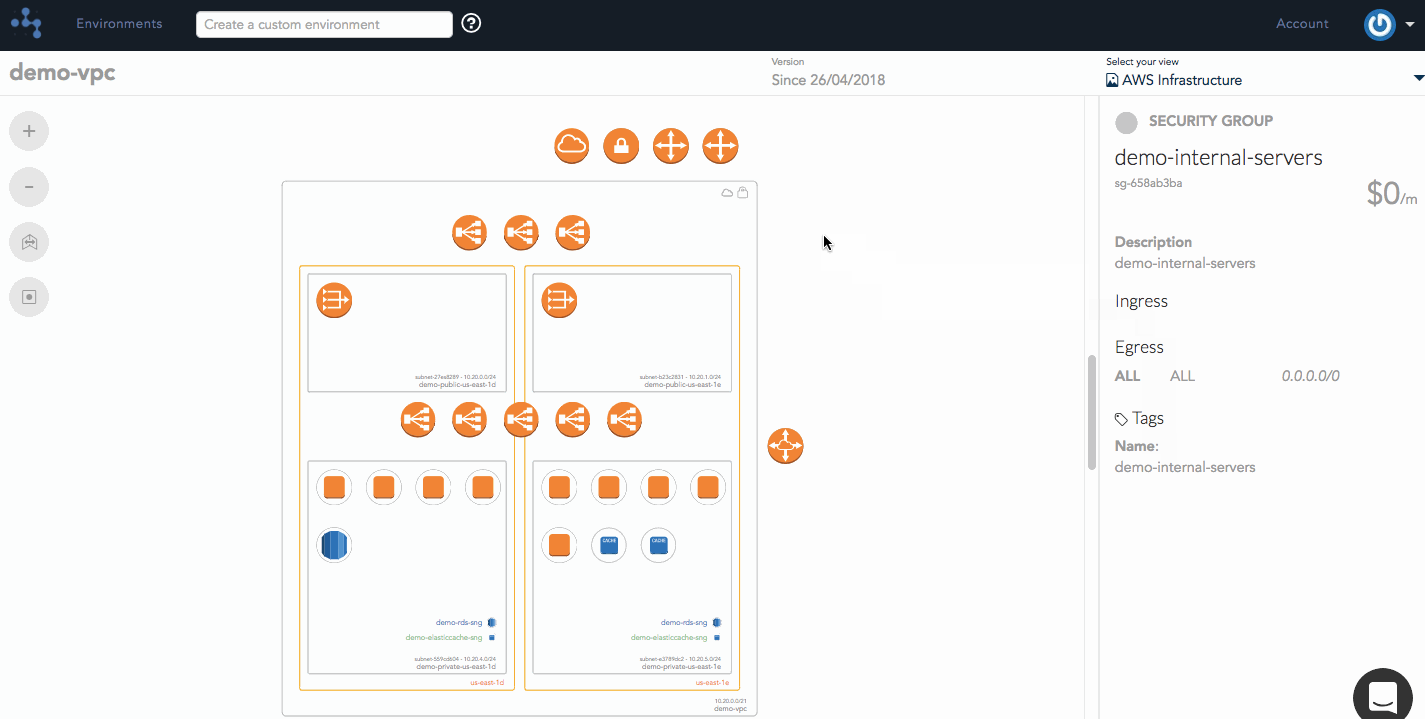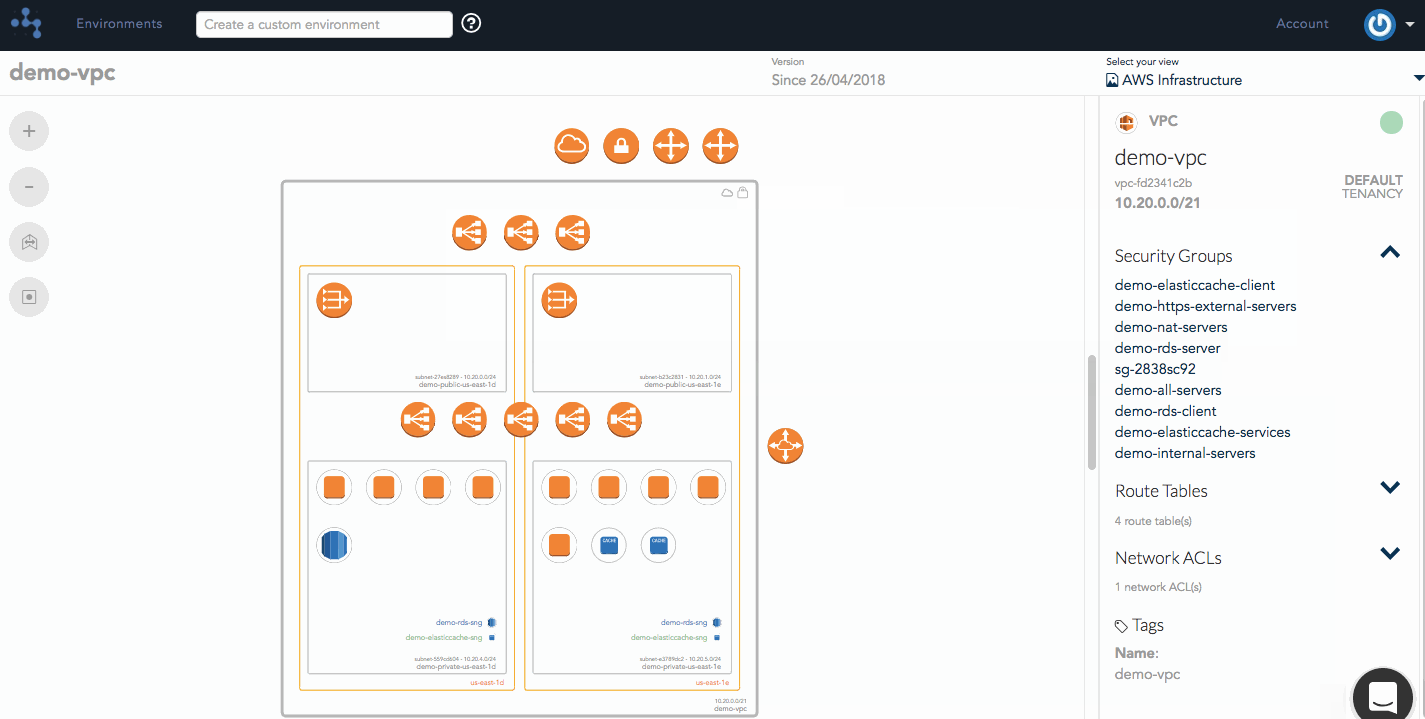
Infrastructure View Highlighting
Our security group highlighting feature allows a user to view all the different security groups that belong to a VPC. You're able to see which instances, load balancers, and other resources that they apply to within the VPC simply by hovering over that particular security group to highlight the connected resources on your diagram.
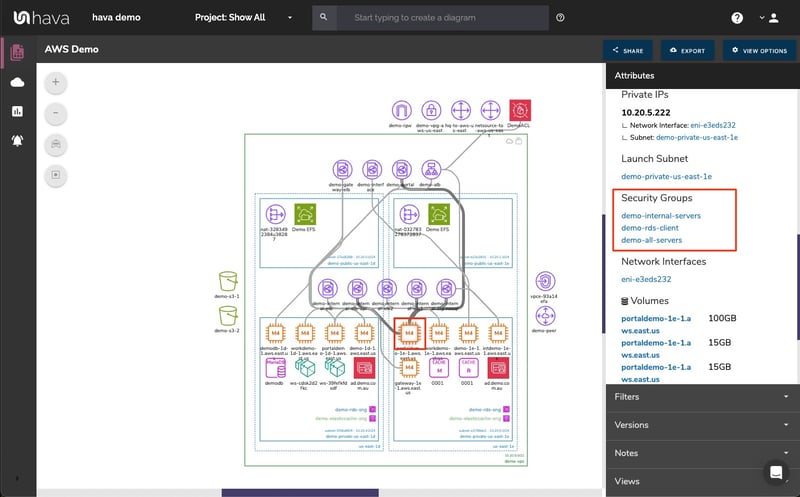
Security Group View
Hava's security view allows you to visualize the configured traffic flows between a collection of Security Group rules and other external resources. At a glance, you should be able to identify anomalies between what's illustrated and what the user expected to be configured. At a deeper level, you'll be able to diagnose misconfigured rules and highlight traffic flows between groups.
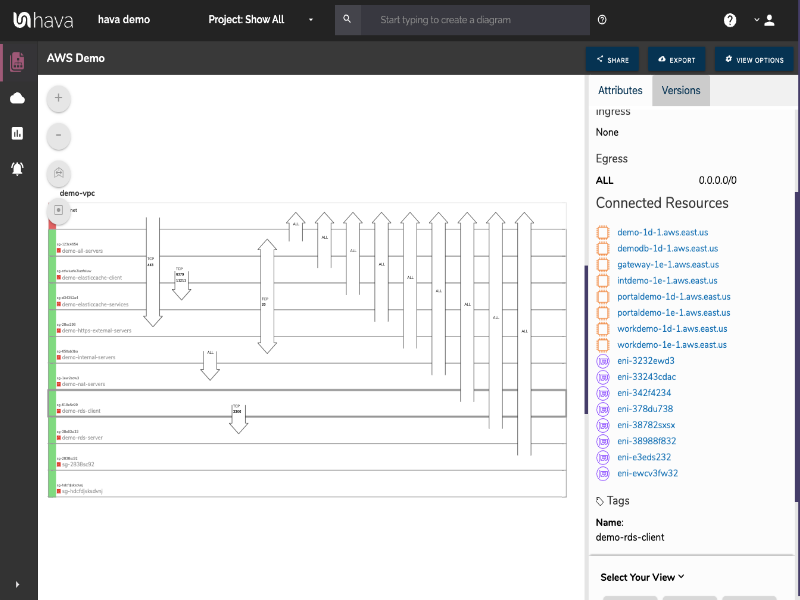
The arrows that you see have been derived from the security group rules that belong to those security groups. You can see the arrow coming from the internet allowing SSH traffic into TCP port 22, and various other protocols allowed between internal groups.
Along with the above two views you also have the ability to export this information via multiple formats such as CSV, JSON, PDF and PNG. These exports are ideal for explaining the configuration to colleagues or potential auditors to clearly illustrate your security groups from the source of truth with no room for human error.